This chapter describes how to configure DRP server agents on Cisco routers. For the Director to be able to efficiently distribute traffic load, it needs to query border routers (or peers to border router) for BGP and IGP metrics. The Director obtains these metrics via the Director Response Protocol (DRP). The chapter contains the following sections:
For more complete information about Director commands, see the chapter "Command Summary and Reference."
When you enable DRP on a Cisco router, the router gains the additional functionality of being a DRP server agent. The router that will also be a DRP server agent must meet these requirements:
- The DRP server agent should be topologically close to each distributed server it supports.
- If the distributed servers assigned to one subdomain or host name are in different autonomous systems, the DRP server agent must have access to full BGP Internet routing tables. For example, the DRP server agent could be a border router or a peer to a border router. The DRP external metric is derived from BGP information. In addition, if you want to use the DRP internal metric, the DRP server agent must have access to full IGP routing tables.
- If the distributed servers assigned to one subdomain or host name are in the same autonomous system, the DRP server agent must have access to full IGP routing tables (but BGP information is not needed). The DRP internal metric is derived from IGP information.
- When you use the DRP internal metric for distributed servers assigned to one subdomain or host name, all of the associated DRP server agents should use the same type of IGP, such as RIP, RIP2, IGRP, or OSPF.
Remember that a DRP server agent can communicate with multiple Directors and support multiple distributed servers.
Perform the following tasks on a Cisco router in global configuration mode to configure the router as a DRP server agent:
Note The router must support the DRP protocol, which is present in Cisco IOS versions 11.2(4)F and later.
Task
| Command
|
|---|
| Step 1 Turn on the DRP agent.
| ip drp server
|
| Step 2 Enable security for DRP by defining a standard access list that permits requests from the Director only.
| access-list number permit [Director-IP-address]
access-list number deny any
|
| Step 3 Ensure that the router accepts DRP queries from the IP addresses associated with the standard access list only.
| ip drp access-group access-list-number
|
| Set up Message Digest (MD5) authentication with passwords as another security measure.
|
|
| Step 4 Enable the DRP authentication key chain.
| ip drp authentication key-chain name-of-chain
|
| Step 5 Set up a key chain, using the same name used in the prior step.
| key chain name-of-chain
key number
key-string text
exit
This sets up an authentication key chain containing one key.
|
| Step 6 Check the configuration with the EXEC command.
| show ip drp
|
The key chain is an encrypted password that helps prevent DRP-based denial-of-service attacks, which can be a security threat. The key chain, a string of characters without spaces, must match the key chain of the Directors it communicates with. If MD5 authentication is configured on a DRP server agent, the Director must be similarly configured to recognize messages from that MD5 authentication-configured DRP server agent, and any other DRP server agents configured for MD5 authentication.
Configuring additional DRP server agents for MD5 authentication is optional.
The following show ip drp output example indicates that all 30 requests were successfully looked up and replied to. If any requests had been denied due to MD5 authorization failing or because of access lists, then "failures" would report denied requests.
30 director requests, 30 successful lookups, 0 failures
This section shows a sample configuration, using the network arrangement in Figure 6-1.
Figure 6-1: Sample Network Arrangement
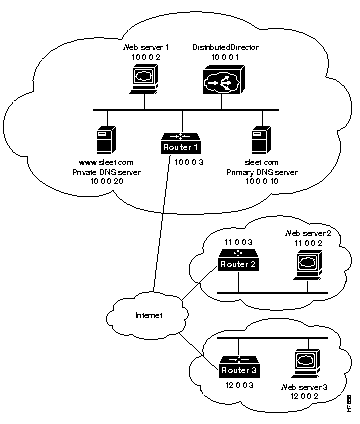
For each router shown in Figure 6-1, you would turn on the DRP server agent with the following global configuration command:
ip drp server
To set up security, you might enter the following global configuration commands on each router.
- To set up an access list, you would enter these global configuration commands:
access-list 1 permit 10.0.0.1
access-list 1 deny any
- Then enter the following global configuration command to ensure that the router accepts DRP queries from the IP addresses associated with the access list only:
ip drp access-group 1
- To set up MD5 authentication with passwords, you must first set up a key chain by entering a sequence of global configuration commands like the following:
key chain violet
key 5
key-string carnation
exit
- This sets up an authentication key chain containing one key.
- Then make this the DRP authentication key chain with the following global configuration command:
ip drp authentication key-chain violet

