|
|

This chapter contains an overview of the CiscoSecure Access Control Server (ACS) 2.1.2 for UNIX (Solaris) software, defines package contents and system requirements, describes features of the software, and provides general information on network security.
The CiscoSecure ACS software is designed to help ensure the security of your network and track the activity of people who successfully connect to your network. The CiscoSecure ACS software uses either the Terminal Access Controller Access Control System (TACACS)+ or the Remote Authentication Dial-In User Service (RADIUS) protocol to provide this network security and tracking.
The CiscoSecure ACS uses Authentication, Authorization, and Accounting (AAA) to provide network security. Each facet of AAA significantly contributes to the overall security of your network:
The CiscoSecure ACS sits on a network that dial-in users and other types of outside users access through a network access server (NAS).

As users log in through the NAS, the CiscoSecure ACS exchanges data and instructions with the NAS, authenticating and authorizing users on the basis of user and group profiles that are stored in either a local or network database. After the CiscoSecure ACS software authenticates and authorizes users for the proper level of network access, it tracks individual user access and stores this information in a database where it can later be retrieved for accounting or analyzing network use.
System administrators authorized to manage the CiscoSecure ACS do so from a network workstation through the web-based CiscoSecure Administrator program.
Users can be granted access to a web-based CiscoSecure User Access program, through which they can change their login passwords.
You can configure the CiscoSecure ACS software to work in conjunction with token card servers and PIX firewall servers.
The CiscoSecure ACS is designed to provide for easy expansion of AAA services in a NAS. It uses relational enterprise databases, allowing an environment in which any number of CiscoSecure ACSes can be distributed among many locations.
For example, if you have multiple main points of presence (POPs), each POP can use its own CiscoSecure ACS. The distributed databases provide the necessary replication of data among the CiscoSecure ACSes. This solution allows for redundancy, user-entry scalability, and performance scalability.
The NAS at each POP can always use its local CiscoSecure ACS as the primary server. The scalable architecture of the CiscoSecure ACS provides that, in the event a NAS is unable to use its primary server, the NAS can also point to two other backup CiscoSecure ACSs. This helps to ensure continuous availability of network resources.
CiscoSecure ACS uses an Administrator program. This interface allows multiple administrators to add users to CiscoSecure ACS. CiscoSecure ACS provides record locking so that only one administrator at a time can modify user information.
Using the CiscoSecure ACS software saves memory in all the access devices and eliminates the need to update every NAS when new users are added, authorization is modified, or users change their passwords.
The CiscoSecure ACS supports user group profiles. This feature allows you to define a group with a set of attributes based on your security policy. When you add a user to that group (defining the user's password in the process), the new user is automatically assigned the attributes for the group. This dramatically simplifies the process of adding a user and makes your security easy to enforce and modify.
The distributed architecture of the CiscoSecure ACS allows you to scale your performance. In a network with multiple POPs, each CiscoSecure ACS supports a primary POP. In a distributed architecture, authentications per second are multiplied by the number of CiscoSecure ACSes in the network. That is, if the performance of CiscoSecure ACS is X authentications per second, when you use 10 CiscoSecure ACSs, you'll achieve 10X authentications per second.
The CiscoSecure ACS supports the following database options for storing group and user profiles and accounting information:
The CiscoSecure ACS supports the following upgrade options:
The CiscoSecure ACS package includes the following items:
The CiscoSecure ACS requires the hardware and software specified in the following sections.
The CiscoSecure ACS requires the following hardware:
Requirements for the workstation on which the web-based interface for the CiscoSecure ACS is run depend on your web browser and operating system. See your manufacturer's documentation. Workstations normally require:
The SPARCstation-based CiscoSecure ACS requires:
 | Caution Do not use a browser that is not specifically listed in the release notes or readme.txt file as being supported. |
The CiscoSecure ACS software is licensed per server. That is, each CiscoSecure ACS requires its own license. You can also use a backup server license to allow sites to run redundant systems to back up system security and accounting information. For details on setting up licensing on your CiscoSecure ACS, see the chapter "Preparing to Install the CiscoSecure ACS Software."
The CiscoSecure ACS software conforms to the following standards and specifications:
To run CiscoSecure, the CiscoSecure ACS network must include these hardware and software elements:
Figure 1-2 shows a typical configuration.

In this example, the NAS, CiscoSecure ACS, external relational database, web browser workstation, and token card server are interconnected. With the appropriate authorization, the CiscoSecure ACS can be managed from any computer on the network running a supported web browser.
CiscoSecure ACS software uses group-and-user information stored in a relational database for Authentication, Authorization, and Accounting. This database is known as the AAA database.
The CiscoSecure ACS software does the actual work of verifying Authentication, Authorization, and Accounting (AAA), and responds to the NAS for access requests by users outside the LAN. Using the TACACS+ or RADIUS protocol, the NAS sends authentication requests to the CiscoSecure ACS, which then verifies the username and password and returns a success or failure response to the NAS.
When the user has been authenticated, a set of session attributes can be sent to the NAS to provide additional security. These attributes can include per-user access lists, specific services that can be used, and session timeout values.
Figure 1-3 illustrates a scenario in which the process of AAA is performed by the NAS and the CiscoSecure ACS.
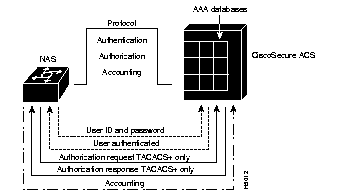
TACACS+ and RADIUS are AAA protocols through which the NAS and the CiscoSecure ACS communicate. You can configure CiscoSecure to support the TACACS+ protocol, the RADIUS protocol, or both. Which protocol combination you enable may depend on the set of AAA features that you want to support. The following table lists the AAA features supported by the two protocols.
| AAA Feature | TACACS+ Support | RADIUS Support |
|---|---|---|
| Web-based administration | Yes | Yes |
| Encrypted password transactions | Yes | Yes |
| Solaris 2.5 or greater support | Yes | Yes |
| Option to disable accounts after failed login attempt count exceeded | Yes | Yes |
| User group membership support | Yes | Yes |
| Accounting support | Yes | Yes |
| S/Key authentication support | Yes | Yes |
| Option to specify maximum sessions per user | Yes | Yes |
| Support for use of common token card servers (CRYPTOCard, Secure Computing, and Security Dynamics, Inc. [SDI]) | Yes | Yes |
| Password aging and configurable warning period | Yes | No |
| Allow/refuse option for remote addresses | Yes | No |
| Option to change user passwords or reject passwords not meeting security requirements | Yes | No |
| Language configurable message catalogs | Yes | No |
| Option for a single TCP connection between the NAS and the CiscoSecure ACS | Yes | No |
| Permit/deny control for X.121 addresses (on a network-wide basis) | Yes | No |
| Permit/deny control for X.121 addresses (on a NAS-by-NAS basis) | Yes | Yes |
To support the use of RADIUS protocols, CiscoSecure supplies RADIUS protocol "dictionaries" that support the sets of "Attribute-Value pairs" for commonly-used versions of the RADIUS protocol. CiscoSecure supplies separate dictionaries to support the attribute sets supported by Cisco IOS Release 11.2, Ascend, and the IETF-RADIUS specification.
Using the CiscoSecure Administrator, you can customize a dictionary's attribute set to suit the access control attributes your NAS is configured to support and assign this dictionary to a group profile or user profile. When users fitting this profile log in through the NAS, the CiscoSecure ACS and the NAS communicate through the RADIUS protocol, using the attributes specified in the customized dictionary to determine the authentication and authorization of the new user, and also store user accounting information.
The CiscoSecure web interface enables you to use Netscape Navigator or Microsoft Explorer to easily set up and modify the authorization and authentication parameters of any group or user on your network. You can assign users to groups that have a set of common configuration parameters. You can then further modify the parameters for each individual user. The CiscoSecure Administrator web interface provides a point-and-click interface to administer the user database. See the chapter "Managing User Authentication and Authorization."
To maintain reliability and security in your network, the AAA features of the CiscoSecure ACS software help you monitor and control:
Authentication allows network managers to bar intruders from their networks. Simple authentication methods use a database of usernames and passwords, while more complex methods use one-time passwords (OTP).
CiscoSecure ACS software uses the TACACS+ and/or RADIUS protocol to authenticate users who dial in to accept usernames or password information sent to a NAS by different protocols such as the AppleTalk Remote Access Protocol (ARAP), Serial Line Internet Protocol (SLIP), Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), and standard Telnet. This broad protocol support provides flexibility for network administrators to define the same or different usernames and passwords for different protocols.
CiscoSecure ACS software supports the following password management features:
Authorization lets network managers limit the network services available to each user and helps restrict access to the internal network to outside callers. It also lets mobile users connect to the closest local connection and still have the same access privileges they would have if they were directly connected to their local networks. Authorization also lets you specify which commands a new system administrator can issue on specific network devices.
The CiscoSecure ACS software also supports:
System administrators might need to bill departments or customers for connection time or resources used on the network (for example, total time connected). Accounting tracks this kind of information. You can also use the accounting syslog to track suspicious connection attempts into the network. The accounting portion of AAA contains:
The billing information includes connect time, user ID, connection location, amount of data transferred, start time, and stop time.
The following features are also supported:
For each user that logs in to the network through the NAS with a distinct ID, you use the CiscoSecure Administrator web interface to set up a user profile in the AAA database. This profile contains all the relevant information that the ACS needs to authenticate, authorize and log accounting information for that user on the network.
When authorized users log on to your network, the CiscoSecure ACS uses the group and user profiles to identify users of a service or a set of services.
As the number of users grows, assigning all the necessary attributes to every individual user becomes time-consuming and unmanageable.
For large groups of users with similar characteristics, you can set up CiscoSecure user group profiles that allow you to set up AAA attributes for large numbers of users at the same time. This means that you can declare common characteristics once and have each user assigned to the group inherit those characteristics when they are assigned to the group. This obviously saves a great deal of time.
One way to manage large numbers of users is to group them together according to the services they will use. Using the web-based CiscoSecure ACS Administrator program, you can modify the CiscoSecure ACS to define each group and authorize it to use the appropriate set of services. You can then add each new user to the appropriate group.
For example, you could restrict access by assigning regular employees and contract employees to separate groups and assigning attributes that allow the regular employees group to dial in at any time and the contract employees group to dial in only from 8:00 am to 5:00 pm Monday through Friday.
With grouping, you can also control the access of users to critical network services. For example, rather than controlling the access to a feature, you could control the ability of a group of users to log onto a specified server.
A group can be a member of another group. In a sales group, for example, the complete sales information group might be a member of a larger group of all sales employees that has access to other services and accounting information.
Grouping can simplify the task of ensuring a secure network in which users have easy access to necessary services and information, but no access to other services, which are unrelated to their jobs. In this way, you can reliably and easily ensure the security of the entire network regardless of its size or complexity.
The passing down of a user group's attributes to its member users is called inheritance.
Within the CiscoSecure ACS, inheritance means that in the absence of specifically assigned attribute values, individual users will have the same attributes values as the group from which they were derived.
Inheritance works differently depending on the AAA protocol being applied:
|
|