|
|

You can configure PIX Firewall by entering commands on your console computer or terminal that are similar in context to those you use with Cisco routers.
Help information is available by entering a question mark by itself for a listing of all commands, or with a command for command syntax. For example:
pixfirewall> int ?
usage: interface ethernet inside|outside 10baseT|100baseTX|auto|100full
interface token-ring inside|outside 4Mbps|16Mbps
You can abbreviate most commands down to the fewest unique characters for a command; for example, you can enter wr t to view the configuration instead of entering the full command write terminal, or you can enter en to start privileged mode and co t to start configuration mode.
In addition, you can enter 0 instead of 0.0.0.0.
The PIX Firewall command interpreter provides a command set based on Cisco IOS technologies. This command set provides three administrator access modes:
By default, the console is in unprivileged mode. You can access privileged mode by entering the enable command. PIX Firewall then prompts you for a password. Enter the default password cisco. When you are done configuring PIX Firewall, change the password with the enable password command. Exit privileged mode by entering the disable command.
You can access configuration mode by entering the configure command. You can then write your settings to flash memory, diskette, or to your console computer from either configuration or privileged modes. Use ^z to exit configuration mode and return to privileged mode. From privileged mode, use the disable command or ^z to return to unprivileged mode. The command prompt changes for each mode.
Configuring PIX Firewall consists of the following steps:
Step 1 Using the terminal or computer you connected to the console port during the PIX Firewall installation, connect to the firewall using a modem program such as HyperTerminal, which is provided with Windows 95 and Windows NT.
Step 2 Once you get to the unprivileged command prompt, which should appear as pixfirewall>, proceed to configuration mode by first entering the enable command and then the config terminal command.
Step 3 Initially configure PIX Firewall using the commands described in the section that follows, "Initially Configuring the PIX Firewall."
Step 4 Exit configuration mode and save the configuration in flash memory with the write memory command.
Step 5 Change the default privileged mode password with the enable password command.
Step 6 Monitor the network interface traffic with the show interface command. If both interfaces show that packets are input and output, then the firewall is functioning. If not, ensure that the interface and route commands are specified correctly.
Step 7 Use the ping command to ensure that hosts on the inside and outside of the network are visible to the firewall.
Step 8 Test the network to ensure that you can ping between inside hosts, between outside hosts, and from an inside host to an outside host.
The configuration is now complete.
You can configure the PIX Firewall from the console or across the network with either Telnet or from a network browser such as Netscape Navigator. Before entering commands on the console, you need to have connected a workstation to the console port and started a modem program so that you can enter the initial configuration commands.
Before you can use Telnet, you need to enter the telnet command. Before you use a network browser, enter the http command. After you add these commands to the configuration, you can perform configuration remotely across the network.
To start a console session, connect the console cable and start a terminal program such as HyperTerminal, which is supplied with Windows 95 or Windows NT. Set the baud rate to 9600, use 8 data bits, 1 stop bit, and no parity. If you are using HyperTerminal, set the port to Com 1 and it is then ready for use.
Access configuration mode and enter the following commands to initially configure the firewall:
Alternatively, you can enter lines 1 through 4 and then complete your configuration with a network browser and the HTTP configuration feature of PIX Firewall. Refer to the next section "Configuring with HTTP." The use of the HTTP configuration feature also requires you to enter the http command as explained in "Configuring with HTTP."
Line 1 indicates that you are using an Intel 10/100 automatic speed sensing network interface card. This statement and that in line 2 set the interface speed. If your system contains 3Com Ethernet boards, replace auto with 10baseT. If your system contains Token Ring cards, replace ethernet with token and auto with either 4mbps or 16mbps.
Lines 3 and 4 assign the IP addresses to the inside and outside network interface cards.
Line 5 assigns a pool of NIC-registered IP addresses for use by outbound connections. Enter a class address such as this example address of 192.168.42.1-192.168.42.254 to assign IP addresses 192.168.42.1 through 192.168.42.254.
Line 6 allows open access for the IP addresses in the global statement.
Lines 7 and 8 let you assign default routes to the inside and outside network interfaces. If your system lets routers advertise default routes, these lines can be omitted. (hops is the number of hops from the firewall to the default router, usually 1.)
Line 9 writes the current configuration to flash memory.
PIX Firewall provides a graphical user interface to help simplify configuration tasks. Once you have specified the network interface speed and IP addresses (as described in the previous section), you need to enter two additional commands and you can then use a network browser, such as Netscape Navigator, to complete the configuration. You can have up to 16 simultaneous HTTP console sessions.
To access PIX Firewall from a network browser, use the http command to give access to a workstation and ensure that the firewall has an IP address other than the default 0.0.0.0 value.
At your workstation, start a network browser. Then open a URL and specify the IP address of the PIX Firewall's inside IP address.
The network browser then prompts you for a user name and password as shown in Figure 2-1.
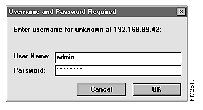
Always use admin for the user name and enter the password you specified with the passwd command. Use the show passwd command to view the current password. The default password is cisco.
The main configuration screen then appears as shown in Figure 2-2.
The troubleshooting information in this section is based on Figure 2-3.
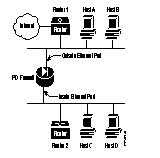
Use the steps that follow to determine that your PIX Firewall is ready for use.
Step 1 Use the show interface command to ensure that the interface and line protocol are up. If the display contains "inside is up," then the interface is functioning on the firewall. If the display contains "line protocol is up," then the cable is correct and connected to the firewall. If both of these are true, ensure that packets are input and output. If this is occurring, the firewall is correctly configured and a cable is attached. However, even with these, the firewall may still not be reachable from other hosts.
Step 2 Use the show ip address command to ensure that the IP address you expect is associated with each network interface.
Step 3 Use the show arp command to see if ARP requests are being processed.
Step 4 Can you ping the inside Ethernet port on the PIX Firewall from a host on the inside network? If no, the problem is on your internal network.
Step 5 Can you ping another host on the same segment; for example, C to D? If no, the problem is on the inside network and not with the PIX Firewall. If yes, check the routing setup on the internal network(s). Check default gateways for the problem, if RIP listening is not in effect.
Step 6 Can you ping the outside Ethernet port from a host on the outside network; for example, from A or B? If no, can you ping another host on the outside network; for example, A to B? If no, the problem is not the PIX Firewall but is on the outside network.
Step 7 Can you ping a host on the outside segment from a host on the inside; for example D to A? If no, check the default gateways to the respective hosts if RIP listening is not in effect. If a router is present on the inside network, hosts on the inside segment must have gateways pointing to the router, and the router must point to the PIX Firewall. For example, the default routes for C and D must point to Router 2, and the default route for Router 2 must point to the PIX Firewall.
Observe the following guidelines during configuration:
|
|