|
|

This chapter provides information on the Cisco Centri Firewall. The information is organized into the following sections:
As the growth of the Internet continues at a rapid pace, more organizations including small to medium businesses need a secure connection to the Internet to protect against increased security risks. The Cisco Centri Firewall provides small to medium businesses with a strong security solution that is tightly integrated with Windows NT and easy to set up and administer.
The New Standard--Centri Firewall defines a new standard in firewall architecture with the Kernel ProxyTM architecture, the first multilayer proxy evaluation technology that runs in the kernel of the Windows NT operating system. Centri Firewall is the only Windows NT firewall with this technology.
Multi-Layer Analysis--At each layer of the TCP/IP protocol suite, the Centri Firewall evaluates network packets using its custom, high-speed protocol stack. This multilayer technique ensures that each network packet and the data it carries are validated against the defined security policy. If a packet fails to pass the security policy at any protocol layer, it is dropped.
Protected Native Stack-- The Centri Firewall runs in the Windows NT Executive, between the native Windows NT TCP/IP stack and the network device driver layer. This separation means that Centri Firewall is not vulnerable to weaknesses within the native Windows NT TCP/IP stack. Also, because Centri Firewall does not alter or replace the native Windows NT TCP/IP stack, the native stack is treated by the Centri Firewall as just another network node residing on the network--an independent virtual host on the same hardware as the firewall. No packets are sent to the native stack unless they are specifically addressed to it, and they have passed all applicable security policies.
Comprehensive Rogue Applet Protection--Centri Firewall detects all (not only one or two like other firewalls) of the major applet technologies being used over the World Wide Web (WWW) today, including Java, ActiveX, JavaScript, and Visual Basic scripts. Centri can be set to block none, all, or specific types, as defined in your security policy.
Comprehensive Hacker Attack Protection--Centri Firewall detects and blocks known cracking methods like IP spoofing, Sendmail attacks, and denial of service attacks. These actions are executed automatically in the Kernel Proxy, and are logged in the event database. Real-time alerts for these events can be set for visual displays, e-mail, or paging.
Focus On Execution, Not Context Switching--Centri's innovative architecture also offers extremely high performance. The Centri's intelligent TCP/IP stack examines the contents of every packet within the kernel space of the Windows NT Executive, eliminating the need to pass packets up to the application space for evaluation. This results in better performance than competing firewalls that spend extra time moving packets to other areas of the operating system for processing.
Use Powerful, Convenient Windows NT Features--Centri Firewall is tightly integrated with the Windows NT operating system to take maximum advantage of Windows NT security features and to seamlessly work in a Windows NT environment. For example, Centri is able to associate the IP address of an internal host requesting a network connection with a Windows NT username. This allows network administrators to assign security policies to Windows NT users, groups, and domains independent of the IP address of the user's computer. This is ideal for a network environment with IP addresses dynamically assigned by a DHCP server.
Simple, Secure Installation--The installation wizard walks the network administrator through the installation and initial setup with easy-to-answer questions. Because Centri's security stance is "that which is not explicitly permitted is denied," nothing is left open unless you want it to be open. The installation and initial setup can be completed in 20 minutes.
Easy Internet Service Configuration--Unlike other firewalls that require you to know and specify each specific protocol used by your applications, Centri does the work for you. Centri comes with preconfigured support for popular network applications and services. In addition, the preconfigured security policies secure a private network from the Internet while allowing users on the private network transparent access to the Internet.
Sensible Approach To Security Policies--Centri's innovative security Policy Builder makes it possible to have expert-level security without the expense of onsite security experts. The powerful combination of Centri's Natural Network ViewerTM and Policy BuilderTM makes securing a network truly simple for the first time. The Natural Network Viewer allows you to drag and drop defined security policies onto network objects. You can apply security policies to NT domains, users, groups, individual machines, and groups of machines residing in defined physical or logical networks. The Policy Builder allows you to create and maintain security policies as decision trees (flowcharts). You can create security policies in an intuitive way that can be understood by non-security experts.
Run Multiple Services on the Firewall Host Machine--Centri's architecture allows network administrators to securely run supported server applications such as Web, E-mail, and DNS on the same systems as the Centri Firewall. This feature simplifies network configuration and reduces hardware costs associated with connecting to the Internet. Supported applications must use the publicly documented Windows NT APIs (running the Cisco Centri Firewall and the Microsoft Internet Information Server on the same Windows NT system is not supported).
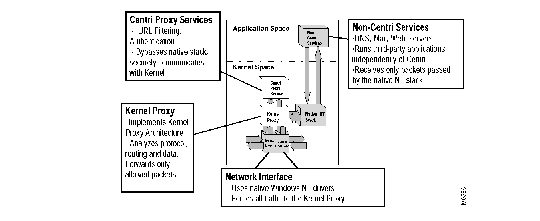
Centri's unique Kernel Proxy architecture provides strong security with high performance on the Microsoft Windows NT platform. With the Kernel Proxy architecture, the Centri Firewall intercepts and analyzes all network traffic between a private network and the Internet. The intercepted network traffic is validated against the security policy before being allowed through the firewall or to applications on the same Windows NT server. Intercepting the network traffic at the device driver layer of the Windows NT operating systems protects the firewall from the vulnerabilities of the native Windows NT TCP/IP stack and offers much higher performance than competing firewalls.
The minimum recommended system requirements for satisfactory performance for most small- to medium-sized organizations are shown in Table 130.
| Item | Minimum Requirement | Recommended |
| CPU | 133 MHz Intel Pentium | 200 MHz |
| RAM | 32 MB | 64 MB |
| Hard Drive | 1GB hard disk drive | 2GB |
| Floppy Drive | 1.44 MB 3 1/2-inches | OK |
| CD-ROM drive | 2x speed | OK |
| Network Adapters | 2 network adapter cards, Ethernet | OK |
| Video Card | Minimum of 800 x 600 resolution at 8-bit color | OK |
| OS | Microsoft Windows NT Server 4.0 | Windows NT Service Pack 2 |
| Product Name | Product Number |
| Centri Firewall, 100 Users | CENTRI-100 |
| Centri Firewall, 250 Users | CENTRI-250 |
| Centri Firewall, Unrestricted Users | CENTRI-UNR |
| Centri Firewall, Upgrade, 100-250 Users | CENTRI-UPG-100-250 |
| Centri Firewall, Upgrade, 100 Unrestricted Users | CENTRI-UPG-100-UNR |
| Centri Firewall, Upgrade, 250 Unrestricted Users | CENTRI-UPG-250-UNR |
| Centri Firewall, evaluation kit for resellers | CENTRI-EVAL-CH |
|
|