|
|
Setting Up Domains and Securing Applications
This chapter contains the following sections that describe how to use the Security Manager and Domain Manager applications:
The Security Manager application allows you to protect your CiscoWorks applications and network devices from unauthorized individuals. In general, this requires you to define what degree of access each group/domain has for each CiscoWorks application that uses security. This can be a time-consuming process, so first determine whether you need to restrict access to any applications. If you do not require security, skip ahead to the next chapter.

With Security Manager, you can set up your CiscoWorks environment to require a login to access each application. This protection ensures that only users who have a valid account can perform tasks such as configuring a router, deleting database device information, or defining polling procedures.
The CiscoWorks security system is turned off upon the first installation or upgrade of CiscoWorks. Until you turn on the authentication checking in the Security Manager, anyone can access any CiscoWorks application without a username or password. Authentication checking requests that users prove their identity by entering a valid CiscoWorks username, and optionally, a password. If you do not possess a valid username and password, you will be denied access.
Before you can protect your applications with Security Manager, you should confirm that device entries exist in the database. To ensure that the device list is updated, you may want to run Sync w/Sybase before setting application privileges. For more information on running Sync w/Sybase, refer to Chapter 6, "Device Management."
Following is an overview of how to use the Security Manager application to protect your network devices and data:
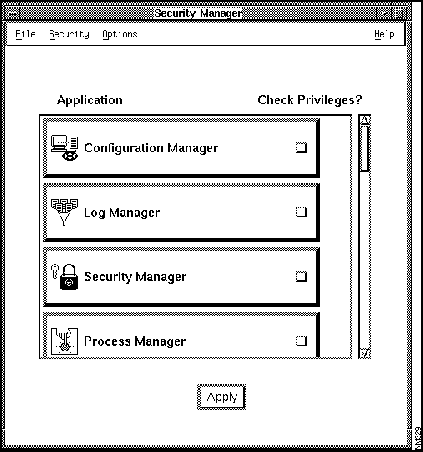
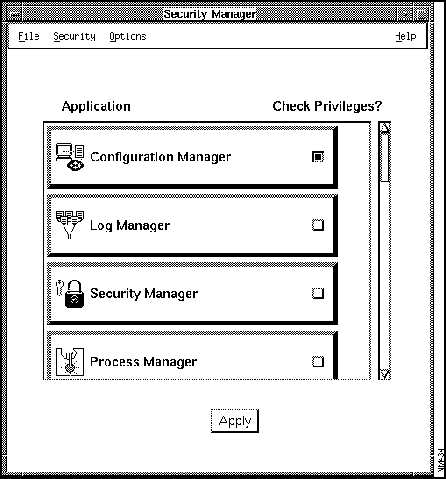
Figure 7-1 illustrates the Security Manager window. Table 7-1 describes its components.
Figure 7-1 : Security Manager Window
Table 7-1 : Security Manager Window Components
Restricting Permissions to CiscoWorks Applications
Table 7-2 lists the Security Manager applications for which privileges can be set, the available privileges for each application, and a brief description of the access privilege. The application names in parentheses are filenames. If you start the application from the command line, enter the filename. For more information on starting applications from the command line, refer to Appendix B, "Troubleshooting CiscoWorks Errors."
The remaining CiscoWorks applications do not require usernames and passwords. These applications are meant to be shared by your network users without restrictions.
Table 7-2 : CiscoWorks Applications and Privileges
The following sections describe how to set up user and group permissions for these applications.
Setting Up the CiscoWorks Default Account
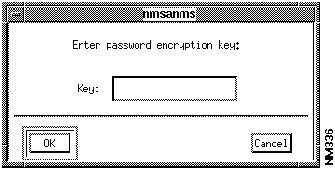
The CiscoWorks software contains a default account password for CiscoWorks applications that access the Sybase database. The administrator password is referred to as the SA (system administrator) password. The SA Password application allows you to change the default account password; you can also use the nmsanms program, a command line interface, to change the default account password. Run the SA Password application (or the nmsanms program) when you are not using the Security Manager application.
Run the SA Password application (or the nmsanms program) in the following situations:
To run the SA Password application application, perform the following steps:
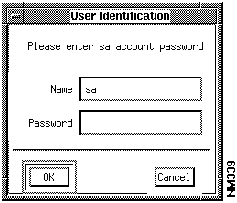
Figure 7-2 : User Identification Window Figure 7-3 : nmsanms Encryption Window Establishing Security Privileges for Users
Using Security Manager, you can add new users to access the CiscoWorks applications that can take advantage of security or authentication checking. The CiscoWorks applications that can take advantage of Security Manager are those that use the Sybase database. You will give privileges to users so they can access secured CiscoWorks applications.
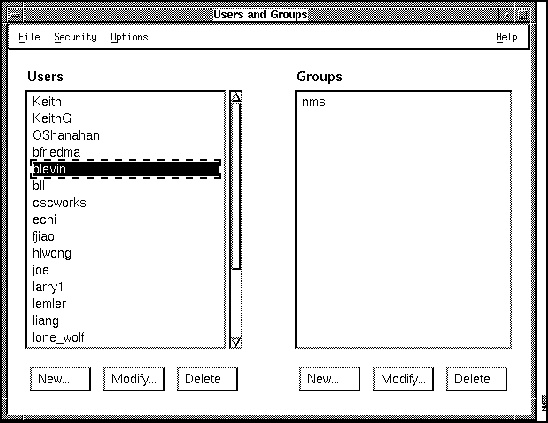
Every user must belong to a group. To authorize users to access applications that have security restrictions, define groups of users that can access each application via their usernames. The first time you access the Users and Groups window, there are no groups or users defined. You must define group names and authorized users for each group.
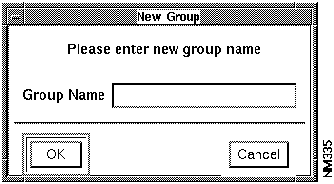
To add new group names to the Security Manager, perform the following steps:
Figure 7-4 : Users and Groups Window
This section describes how to edit existing group names, if necessary. After you finish adding and editing your group names, you will need to add your usernames.
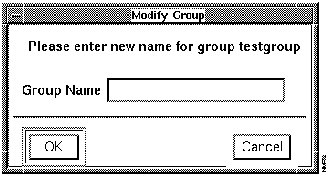
To change the name of a group, you must access the Security Manager and edit an existing group name. The relationship between the users and groups remains unchanged. In other words, users affiliated with the previous group name automatically move to the new group name.
To edit group names in Security Manager, perform the following steps:
Figure 7-6 : Modify Group Window If you are setting up first-time group and user permissions, continue with the section "Adding New Users" later in this chapter.
To remove security permissions for an entire group, delete the group name from the Security Manager application. After you delete the group name, all users in that group will no longer have privileges assigned to that group.
To delete group names from the Security Manager, perform the following steps:
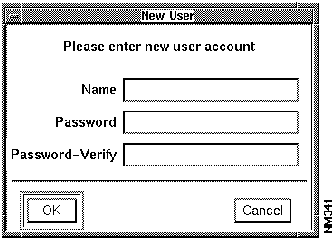
In order to grant users permission to access protected applications, you must enter every user account name (or username) that receives permission to use the CiscoWorks applications.
To add new usernames to the Security Manager, perform the following steps:
Figure 7-8 : Group List Window To change the password of a user, you need to access the Security Manager application. The relationship between the users and groups remains unchanged. The previous groups affiliated with the old username will be assigned to the new username.
To modify passwords in Security Manager, perform the following steps:
Figure 7-9 : User Identification Window Figure 7-10 : Modify Password Window To remove security permissions for a user, you must delete the username from the Security Manager application. After you delete the username, this individual will not be authorized to access the CiscoWorks applications previously indicated.
To delete usernames from the Security Manager, perform the following steps:
The Security Manager authorizes groups to access CiscoWorks applications based on the permissions set in the Security Manager application. Therefore, you need to connect each user to a group. Users then get permission to the application because they are part of a group.
With the Users and Groups window, you can add an individual user to a group or you can add several users to a group at one time. Each of these procedures is described in the following subsections.
Adding an Individual User to a Group
To connect an individual user to a group, perform the following steps:
Figure 7-11 : Group List Window Adding Several Users to a Group
To connect several users to a group at once, perform the following steps:
Figure 7-12 : User List Window Viewing User and Group Relationships
Use the Users and Groups Summary window to check your group assignments. This window allows you to sort by groups or users. Sorting by groups provides a quick look at all user accounts with this group's privileges. Sorting by users provides a quick look at all groups associated with one user.
To display your user or group assignments, perform the following steps:
Figure 7-13 : Users and Groups Summary Window Domains are logical collections of devices, just as groups are collections of people. A device is any network entity that contains an SNMP agent. (Devices generally include routers, bridges, or communication servers.)
Creating domains gives you the flexibility to establish a new sphere of security because groups can be assigned privileges according to their connected domain. By incorporating the use of domains, you can allow a local network center to assign privileges for its own devices. The ability of a user to exercise one or more features of a given application is now defined by the group and domain association.
Upon installation, CiscoWorks automatically creates a World domain, which contains all the devices listed in the database. The World domain is predefined and cannot be deleted.
Depending on your needs, you can establish and modify other domains by using the Domain Manager application. For example, consider a large business whose expanding financial hub is located in New York. As a network administrator, you determine a need to protect the New York device configurations and inventories by securing the CiscoWorks applications that can potentially access them. Therefore, you establish the group of devices in New York as its own domain.
Users of the World domain can look into the New York domain to see its devices, but are denied any other privileges. However, New York users are also part of the World domain, so they can exercise the same privileges granted to others in the World domain.
Privileges to devices for users in New York depends on the definitions set by the New York-based network administrator. The network administrator assigns the application-specific privileges (such as read-only or execute) by using the Security Manager application.
Although a user can only belong to one group, a single group can contain many users. By applying this feature, the New York-based administrator decides to govern access to devices even further. Application-specific privileges can be assigned to groups to grant or restrict varying levels of access. In the New York domain, the administrator determines that only users of a specified group are granted the special privileges to modify the configuration files on selected routers. Next, the administrator creates a second group whose users are granted the application-specific privileges needed to modify other router information. Groups with other levels of privileges to other applications can be created or modified as the needs of the domain determine.
The net result is that corporate-wide users can view devices in the New York domain. But access to New York devices is restricted to its connected groups. Each connected group is further restricted to the application-specific privileges that were granted by the New York-based network administrator who toggled on each application-specific privilege in Security Manager.
If you want to learn how to create additional domains and the other functions of Domain Manager, go to the next section, "How Domain Manager Works." If you want to connect the default World domain (or other domains that may already exist) to the groups you established in the previous section, perform the following steps:
Figure 7-14 : Domains and Groups Window
Figure 7-15 : Group List Window The Domain Manager application enables you to assign meaningful alias names to groups of devices. Using the various alias domain names you created to manage your network, you can use other CiscoWorks applications to focus on certain domains in order to complete network management tasks.
You can use the Security Manager application to assign group privileges to certain domains. For example, a domain named "North America" might only allow a group called "America-admin" to perform configuration management on these Cisco devices.
Other applications can use domains efficiently to perform their tasks. The Domain Manager communicates domain information to the following CiscoWorks applications:
The Domain Manager sends update messages to these applications, so the domain name and device information is accurate at any given time.
Figure 7-16 illustrates the Domain Manager window. Table 7-3 describes the components in this window.
Figure 7-16 : Domain Manager Window
Table 7-3 : Domain Manager Window Components
You can perform the following tasks with the Domain Manager application:
Adding New Domains and Associating Devices with Domains
Part of the process of creating domains, or groups of devices associated to an alias, is to first create a domain name and then associate devices with that domain name.
There are three ways to add a new domain to CiscoWorks:
The following sections provide procedures for each of the tasks.
To create a domain, perform the following steps:
Creating a Domain from an Existing One
You can create a new domain by copying devices from one or more existing domains. To copy an existing domain, perform the following steps:
Creating and Importing an ASCII File with Domain Information
To create an ASCII file that contains domain data and import it into the Domain Manager, perform the following steps:
Changing the Name of an Existing Domain
To change the name of an existing domain, perform the following steps:
Adding or Deleting Devices to Existing Domains
To add or delete devices associated with an existing domain, perform the following steps:
To delete domains from the Domain Manager, perform the following steps:
To view which devices comprise the domain, perform the following steps:
Establishing Access to Applications
After you created users and groups and connect them to domains, you are ready to establish access to applications, a process called authentication checking. This section describes how to establish user-group permissions and how to set up authentication checking to require login information.
To establish user-group permissions, following these steps:
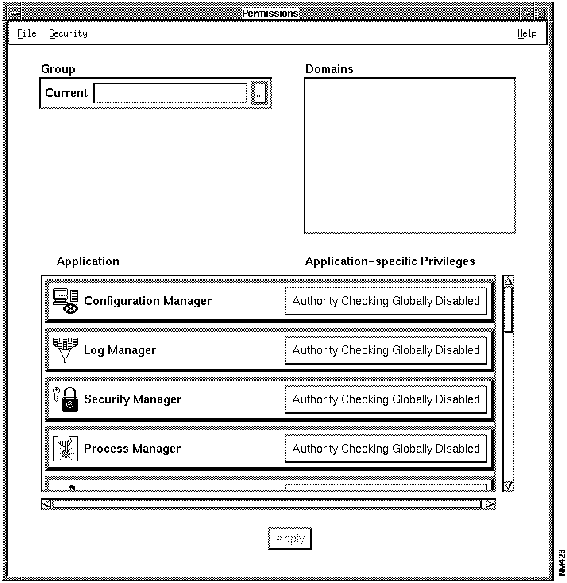
Figure 7-17 : Protected Application Figure 7-18 : Permissions Window Accessing Secured CiscoWorks Applications
Depending on the application that has authentication-checking enabled, you may be required to log in to an application before receiving access. You can log in to CiscoWorks applications in two ways:
Logging in to CiscoWorks Applications
Use the CiscoWorks Login application to log in to use any secured application for which you have permissions. You will be asked for your username and password only once.
The next sections describe the two login scenarios.
Logging in before Accessing CiscoWorks Applications
To log into all CiscoWorks applications you have access to, perform the following steps:
Logging in after Accessing CiscoWorks Applications
If you do not wish to use the Login application, each CiscoWorks application you enter will prompt you for your user identification information.
To log in to any CiscoWorks application for the first time (without the Login application), perform the following steps:
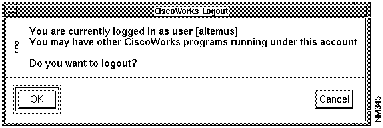
Logging Out of CiscoWorks Secured Applications
To ensure network security, log out of the CiscoWorks applications after you are done using them. You need to perform this procedure only if you have previously logged in using the Login application.
If you select Logout and you have not previously used the Login application, you will receive the following error message: "There is no CiscoWorks login for this process. Logout is not needed."
To log out of CiscoWorks applications, perform the following steps:
Figure 7-19 : CiscoWorks Logout Window The TACACS Account Manager application maintains the TACACS password file on UNIX hosts that act as TACACS security servers. Terminal Access Controller Access Control System, or TACACS, controls Internet host access from terminals using dial-up lines. The TACACS Account Manager allows you to easily create and update TACACS accounts in a graphical user interface.This application also creates computer-generated passwords. Use this application to designate which users have access to your security server.
The TACACS user can perform numerous commands on Cisco devices. For more information on tacacs-server commands, refer to the Router Products Configuration Guide or the Router Products Command Reference publication.
For information on the TACACS daemon, refer to Chapter 9, "Using CiscoWorks Process Manager."
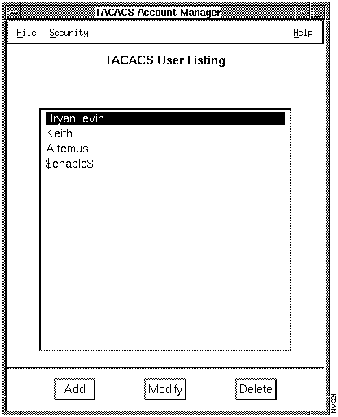
Figure 7-20 illustrates the TACACS Account Manager window. Table 7-4 describes its components.
Figure 7-20 : TACACS Account Manager Window Table 7-4 : TACACS Account Manager Window Components
Add or Edit TACACS User Window
Figure 7-21 illustrates the Add a TACACS User window. The Edit a TACACS User window is the same except the window title and the ReadWrite permissions to each field are different. Table 7-5 describes its components.
Figure 7-21 : Add a TACACS User Window Table 7-5 : Add a TACACS User Window Components
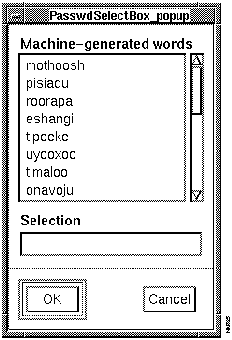
Figure 7-22 illustrates the PasswdSelectBox_popup window.
Figure 7-22 : PasswdSelectBox_popup Window To add a TACACS user, perform the following steps:
Component
Subcomponent
Description
File
Print
Exit
Prints a snapshot of the window.
Exits the current window.
Security
Change User
Privileges
Enables user to change user ID.
Provides current user privileges.
Options
Users and Groups
Domains and Groups
Permissions
Opens a subwindow that allows you to create, modify, and delete users and groups; and to add users to groups.
Opens a subwindow that allows you to assign domains to groups, or delete domains from groups.
Opens a subwindow that displays the application authority status for selected groups and domains. This window allows you to assign specific access privileges of a given application to a specific group/domain combination.
Help
On Version
On Security Manager
Displays the CiscoWorks version information for this application.
Provides help text on the current window.
Check Privileges toggle buttons
Enables authentication checking on the corresponding CiscoWorks application.
Apply
Confirms authentication checking for the CiscoWorks applications whose Check-Privileges buttons were enabled. Applies changes to the database.
Application
Available privileges
Description
Configuration Management (nmconfman)
Execute
Write Password
Read Password
File To Database
Compare Configs
Delete from Database
Device to Database
Database to Device
Browse Config File
Edit Config File
User can execute this application.
User can download a configuration file to a router.
User can access files or data, but not modify them.
User can copy a configuration file from a disk to the database.
User can view configuration differences in the database.
User can permanently remove a configuration file from the database.
User can upload a running configuration file to the database.
User can download an edited configuration file to a router.
User can read an uploaded configuration file.
User can make changes to a given configuration file.
Log Manager (nmlogman)
Execute
Delete log records
User can open this application.
User can permanently remove log messages.
Security Manager (nmadmin)
Execute
Add Groups
Add Users
User can open this application.
Allows creation of new group access.
Allows creation of new user access.
Process Manager (nmproc)
Execute
Start/Stop Process
User can open this application.
User can alter Process Manager functions.
Device Management (nmdevman)
Execute
Write to Sybase
Modify SNMP comm-string
Modify Line Password
Modify Enable Password
User can open this application.
File or data changes are permitted.
User can view and change the community string.
User can view and change the Line Password
User can view and change the Enable Password.
Device Monitor (nmdevmon)---SunNet Manager platform only
Execute
Configure Device
User can open this application.
User can alter Device Monitor functions.
Sync with Sybase (nmsync)
Execute
User can open this application.
Device Polling (nmpoll)
Execute
Modify Polling
User can open this application.
User can alter Device Polling functions.
Polling Summary (nmsummary)
Execute
Modify Polling
User can open this application.
User can alter Polling Summary functions.
AutoInstall Manager (nmautoinst)
Execute
Modify Config
View Config
User can open this application.
User can change the configuration.
User can see the configuration, but not change it.
Software Library Manager (nmswman)
Execute
View Device Inventory
Import Software
Edit Software comments/alias
User can open this application.
User can view a list of all devices in all domains.
User can copy files from another directory (disk or Flash memory of a device) into the CiscoWorks database.
User can add comments to the configuration file.
Software Inventory Manager
(devinventory)
Execute
Update Device
Update Inventory
User can open this application.
User can download system or microcode image to a specified device.
User can edit the device inventory seen from within Software Management.
Device Software Manager (nmdevman)
Execute
Reload Device
Upgrade Device
Edit Software Comments
User can open this application.
User can reload a device.
User can replace existing software or microcode in the device with a version from Flash memory.
User can change comments associated with the operating system.
Domain Manager (nmdomain)
Execute
Delete Domain
Modify Domain
Add Domain
User can open this application.
User can permanently remove a domain.
User can change the domain organization.
User can create a new domain.
Global Command Manager (nmscheduler)
Execute
Delete Commands
Modify Commands
User can open this application.
User can delete configuration commands from a specified router or set of routers.
User can change configuration commands from a specified router or set of routers.
Global Command Scheduler (nmgcmd)
Execute
Delete cron
User can open and run this application.
User can permanently remove the cron file.
TACACS Account Manager (nmtacacs)
Execute
Schedule
Modify Accounts
User can open this application.
User can schedule a task.
User can change (modify, add, or delete) the ownership of TACACS accounts.
hostname% cd $NMSROOT/etc
hostname% su directory_owner
Password: password
hostname% cp /dev/null ncspwd
hostname% chmod 660 ncspwd
hostname% exit
%
$NMSROOT/bin/nmsanms
%
ls -l $NMSROOT/etc/ncspwd
%
more $NMSROOT/etc/ncspwd
![]()

Component
Subcomponent
Description
File
Import
Print
Exit
Opens the File Selection Box window, which allows you to open an ASCII file to import domain information.
Prints a snapshot of the current window.
Exits the current window.
Security
Change User
Privileges
Enables you to log in again as another user.
Displays the current user's security privileges.
Help
On Version
On Domain Manager
Displays the CiscoWorks version information for this application.
Provides help text on the current window.
Domains
Displays list of current groups of devices.
Domain Devices
Displays list of current devices within the domain selected.
New
OK
Add Devices
Copy Domain
Cancel
Creates a domain containing the added devices or, if no devices are added, creates a domain without any devices.
Creates new domain names. Allows you to add devices or copy an existing domain.
When a new domain name is specified, allows you to copy all the device information from an existing domain to the newly established one.
Closes the window without saving any changes.
Modify
Allows you to edit the name of an existing domain.
Delete
Deletes domain names from the scroll window. Updates other CiscoWorks applications on any changes to domain list.
Add
Adds devices to the selected domain.
Remove
Removes devices from the selected domain.
# CiscoWorks 2.0 Domain Creation File
New_domain_name
Device_1
Device_2
Device_3
Device_4
![]()
![]()
![]()

Component
Subcomponent
Description
File
Print
Exit
Prints a snapshot of the current window.
Exits the current window.
Security
Change Domain
Change User
Privileges
Enables you to view devices in another domain.
Enables you to log in again as another user.
Displays your current privileges.
Help
On Version
On TACACS
Provides information on the application version.
Provides information on the current window.
TACACS User Listing
Displays current list of UNIX TACACS users.
Add
Adds new TACACS user data, including TACACS name, user's full name, access ID, user ID, password, and account expiration date.
Modify
Edits TACACS user data, including TACACS name, user's full name, access ID, user ID, password, and account expiration date.
Delete
Deletes TACACS user data.
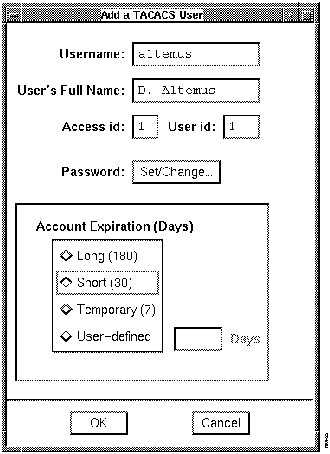
Component
Subcomponent
Description
Username
Displays TACACS username.
User's Full Name
Displays user's name. For reference only.
Access ID
Displays current access rights to Cisco devices, if defined.
User ID
Displays numeric user ID in UNIX for system administrator convenience. Not used in TACACS.
Password
Set/Change
Sets or changes the current user password from a user-entered password or generated list of passwords.
Account Expiration (Days)
Long (180)
Short (30)
Temporary (7)
User-defined
Specifies how long the TACACS password is valid.